AWS Web Application Firewall (WAF) can be a nifty little tool in your defense-in-depth approach. Even the basic rule sets make it considerably challenging for your typical script kiddies to cause much nuisance.
Enabling the AWS-AWSManagedRulesCommonRuleSet can cause some legit traffic
to be blocked since oversized traffic (with body size over 8,192 kB) and traffic
without a user-agent header is blocked by default.
In such cases, it can be incredibly useful to have the capability to look through the CloudWatch logs to understand why certain traffic is being blocked.
We can query the relevant CloudWatch Log group using the AWS Management Console. It looks
something like this:
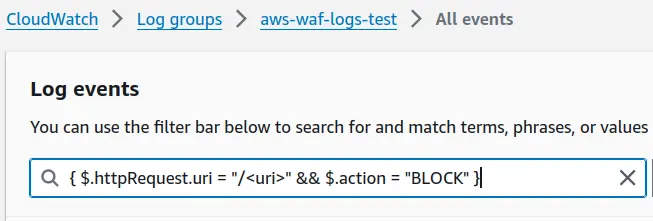
I’ve been using the following query to investigate the BLOCK events of
interest:
{ $.httpRequest.uri = "/<uri>" && $.action = "BLOCK" }
While testing, it is a better idea to try to reproduce the BLOCK events from
your browser or curl so you can then filter more precisely using your IP:
{ $.httpRequest.uri = "/<uri>" && $.httpRequest.clientIp = "<clientIP> && "$.action = "BLOCK" }
In some cases, it can be helpful to also filter by the HTTP Method type:
{ $.httpRequest.uri = "/<uri>" && $.httpRequest.httpMethod = "POST" && $.httpRequest.clientIp = "<clientIP>" && $.action = "BLOCK" }
